Cyberattacks against the energy sector are growing in both number and sophistication. With more than a dozen small utilities located near critical infrastructure targeted in the past year, there are steps that companies can take to minimize their risk and protect their consumers despite the lack of budget or resources.
Cyber-security Is A Business Risk, not an IT problem – Don’t get caught offguard!
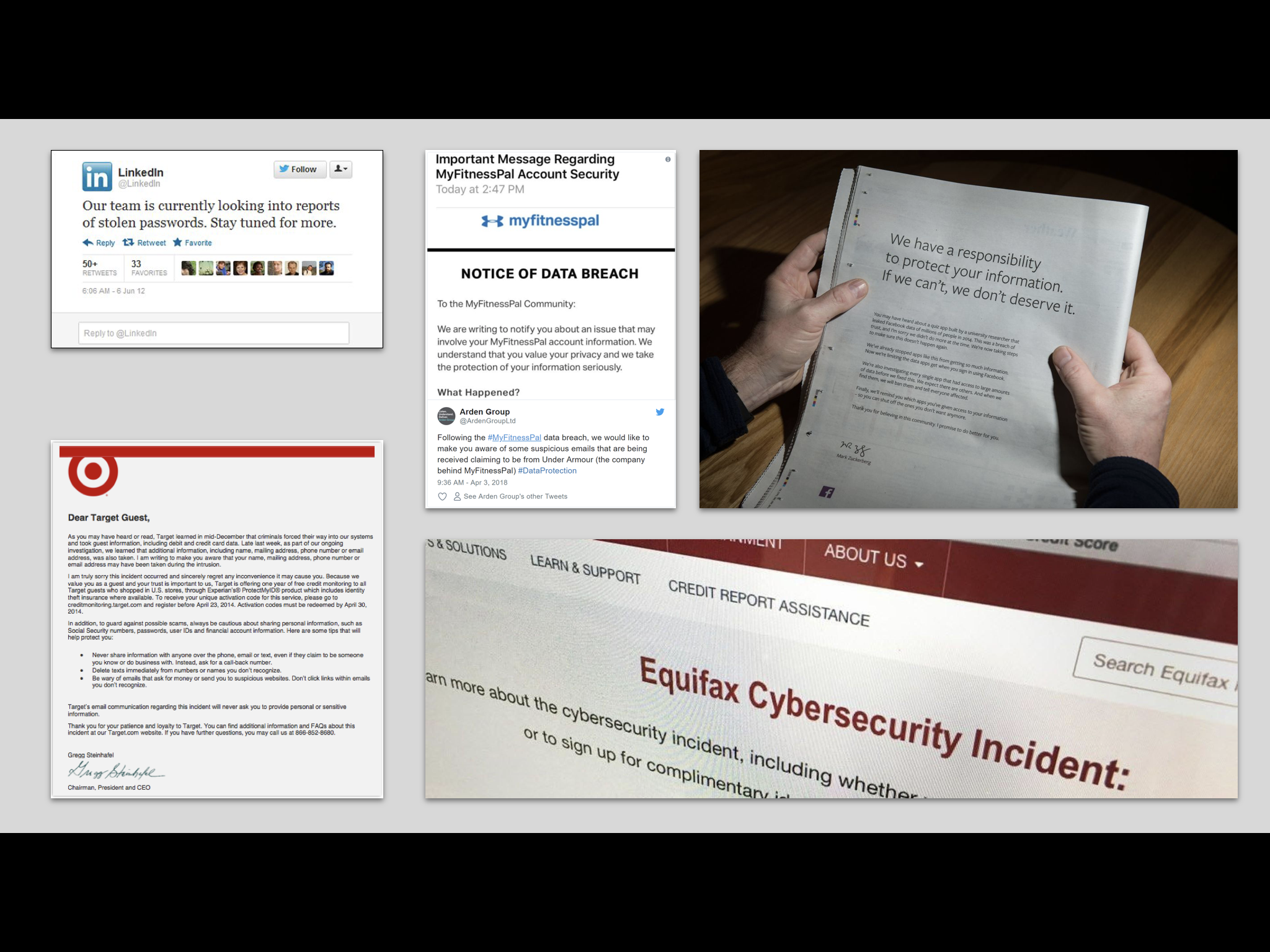
Steps you can take now to prepare for the next data breach that won't cost a lot of money
Just tell me what I need to know when you find out!
Each state in the U.S. has their own individual laws as to when a company must report a data breach. In addition, there are federal laws and EU laws that likewise dictate when companies need to disclose.
On September 1, 2018, Colorado will enact the toughest law yet, giving companies 30 days to provide notice of a breach involving personal information belonging to Colorado residents. Most states mandate 45 or 60 days.
According to The Wall Street Journal, "Colorado also expanded the definition of personal information to include biometric data, driver’s license numbers, passwords and other items. In other state laws, personal information is often limited to a first name or initial and last name in combination with an identifier, such as a Social Security number."
Just this week, Air Canada discovered a breach and responded within days of discovering it. You can see their response below to the people who they believe were affected. It timely and clearly explains:
- What happened;
- The steps the company took to limit the breach; and,
- What they need their customers do to further protect themselves.
Your system will be breached. It is not a matter of IF, it will be a matter of WHEN. To prepare your company needs to create the protocols to MONITOR your systems and develop the PLANS to respond. This includes creating the TEAM and creating SIMULATED responses.
In 2017, a data breach compromised the personal information of 147.9 million Equifax customers. The company was not prepared for the breach and failed in their response, leaving peoples personal data exposed.
if the law in your state or for your industry is unclear, company's in the U.S. should use the European Union’s General Data Protection Regulation (GDPR), which went into effect in May, as guidance which requires companies to disclose a breach within 72 hours of discovering it. Companies, both large and small, should now put the plans in place and prepare for the next attack.
AIR CANADA EMAIL RE. DATA BREACH
28 AUGUST 2018
We recently detected unusual log‑in behaviour with Air Canada’s mobile App between Aug. 22‑24, 2018. We immediately took action to block these attempts and implemented additional protocols to protect against further unauthorized attempts. As an additional security precaution, we have locked all Air Canada mobile App accounts to protect our customers’ data.
Am I affected?
As a result of our analysis, we are confident your account was not affected by these unauthorized attempts. As an additional security precaution however, we have locked all Air Canada mobile App accounts to further protect customer data.
To reactivate your Air Canada mobile App account, please see the instructions below or follow the prompts the next time you log into your Air Canada mobile App.
Your privacy and the protection of your data are extremely important to Air Canada. Our security is multi‑layered, and we work with leading industry experts to continuously improve our practices as technology and security procedures evolve.
Reset your password
Please reset your password to resume using Air Canada’s mobile App and mobile products with confidence.
Your new password must be a minimum of 10 characters. Here are some helpful tips in creating your new password:
• Minimum of 10 characters which must contain at least 1 uppercase letter, 1 number, 1 symbol/special character, 1 lowercase letter
• Do not use your old password
• Do not use your name or something easily associated with you
• Do not use your Air Canada mobile App password with other accounts
You can reset your password by following the prompts when you next log‑in to your Air Canada mobile App, or you may reset your password now or you may also go to https://services.aircanada.com/portal-web/mobile/profile?action=resetpwd&locale=en
For more information
We regret any inconvenience this has caused. If you have questions, please refer to additional information posted on aircanada.com
Sincerely,
Catherine Dyer
Senior Vice President, Chief Information Officer
Air Canada
How safe is our nation’s food supply?
Equifax and the SEC are today’s current cyber-disturbance. But what about our food supply. Congress, in 2010, enacted the Food Safety Modernization Act (FSMA). The law drastically updates how our food is regulated. It creates guidelines for food manufacturers and processors to follow in the processing, producing and handling of food, from harvesting to processing, warehousing and distribution. The federal government however, is still trying to figure out how to enforce the FSMA. The most recent rules focus on preventing the intentional adulteration of food in the supply chain.
Today, we are still vulnerable to attack
Cyber-terrorism is a reality, How are you going to deal with it?
It is not a matter if you will be hacked it is a matter of when and am I prepared.In preparing for a crisis around cyber terrorism? know the law and which laws dictate how your company responds and to whom. Know what you want to say and how quickly you will respond after a reach. Know the influencers and key stakeholders to make sure you to not ignore key people in responding to an attack
Exposure is the new reality
Naked & Exposed We Are All At Risk Of Attack, But Are You Prepared?
From toys to medical devices, the world is a more connected place, exposed to hackers and other threats, that can result in serious injury or damage, both physically and to your financially to your reputation. We are naked and exposed and vulnerable to the risks of living in a connected life in the Internet of Things (IoT). While politically fragmented, Friday's attack proves our world is more connected than ever.
Limiting Reputational Risks When Information Is Breached
Businesses today do not have the luxury of waiting 30 days let alone thirty minutes to notify its stakeholders of a breach in cyber security. CEOs along with the CMO, CIO and CLO must work to create effective and swift protocols to deal with data breaches to limit legal liability risk and risk to the company’s reputation.